Biometric Security


Fingerprint & Security Keys
We’re not far off from biometrics becoming commonplace in our everyday lives. In fact, it already is. Biometrics unlocks your phone, pays bills, grants access, and so much more — all by identifying your unique physical characteristics.
Why Biometrics
Because physical features such as fingerprints and pupils are so difficult to forge, biometrics is a strong security solution, though we see biometrics as part of a comprehensive security solution that might also include a password and/or physical device such as a key, card, or token. In the workplace, biometrics can be part of a strong security protocol for access to internal systems, files, information, and data. And it can be as simple as touching a finger or looking into a camera lens.


For large organisations, biometrics can be an effective way for IT to manage security protocols for employee access, privileges, and passwords.
Without getting too techy . . .
Like anything, biometrics is only as good as its weakest link. So it’s important that the biometric data collected, stored, or transferred is secure and accurate. But how?
Biometrics 101
Learn why biometric security is needed and what technology is used to secure your biometric information.
Compliance with FIDO Technology
The latest industry standard for fast and secure authentication.
Support for Enterprise Applications such as Windows Hello™ and Windows Hello™ for Business
Ideal for enterprise deployment and easily integrated into current IT infrastructure. Users keep their key for secure login, while IT can easily manage employee access, privileges, and passwords.
Secure Encryption and Transfer of Data
Advanced fingerprint technology such as Match-in-Sensor™ securely stores encrypted fingerprint data in the sensor module, whereas the older Match-on-Host system transfers unsecured data between the sensor and host device.
Anti-Spoofing Technology
Delivers results above the industry standard for false rejection rate (FRR) and false acceptance rate (FAR).
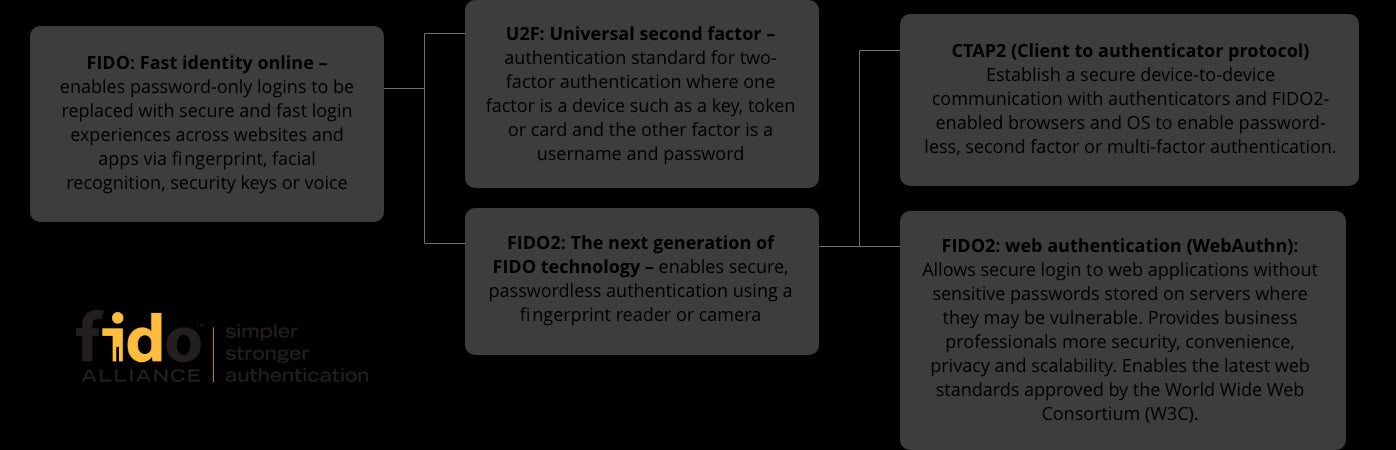
Authentication terminology and what it means
Why risk it?
Data loss accounts for billions of dollars in losses every year, as well as potential damage to a company’s reputation. As the Verizon 2017 Data Breach Investigations Report (DBIR) states, "81 percent of hacking-related breaches leveraged either stolen and/or weak passwords."

While no security solution can guarantee full protection, biometrics is yet another strong link in your security chain. In addition to the inherent uniqueness of an individual’s biometric data (and therefore the level of security this offers), biometrics offers a passwordless solution.
“More than 12M people may be affected by latest medical data breach. Why those patients are now vulnerable.”
Jared Weber, USA Today
“CBP says traveler photos and license plate images stolen in data breach.”
Zach Whittaker
“Over 10 Million people hit in single Australian data breach: OAIC.”
Asha Barbaschow
“Third party data breach to blame for data leaks of major hotel chains.”
Scott Ikeda, Cyber Security News
“Police investigate University of South Wales data breach.”
ITPro Newsletter
“A cyber forensics team has been called in to investigate breaches that exposed nearly 20 million patient records."
Connor Jones


